Amiibo: Difference between revisions
No edit summary |
No edit summary |
||
| Line 13: | Line 13: | ||
The NFC 32bit password for the PWD_AUTH command(for enabling write-access to the encrypted NFC pages / etc), appears to be generated from unknown data that doesn't change when the Amiibo data pages are being updated. | The NFC 32bit password for the PWD_AUTH command(for enabling write-access to the encrypted NFC pages / etc), appears to be generated from unknown data that doesn't change when the Amiibo data pages are being updated. | ||
Each page is 4-bytes, the following is the structure of the NFC | The following NTAG215 commands are used when reading an Amiibo: | ||
* GET_VERSION | |||
* READ, startpage=0x03 | |||
* PWD_AUTH | |||
* FAST_READ: startpage=0x00, endpage=0x3B | |||
* FAST_READ: startpage=0x3C, endpage=0x77 | |||
* FAST_READ: startpage=0x78, endpage=0x86 | |||
Therefore, *all* pages from the Amiibo NFC tag are read, including the configuration pages at the end. | |||
Each page is 4-bytes, the following is the structure of the NFC pages: | |||
{| class="wikitable" border="1" | {| class="wikitable" border="1" | ||
|- | |- | ||
Revision as of 16:45, 15 April 2015
Amiibo are NFC figures made by Nintendo, used in games in different forms (different in each game). It can be used with the New3DS and the Old3DS with an IR peripheral.
Technical specifications
See also here.
Specifications can be found on this image, which is a compilation of screenshots made by scanning a Samus amiibo with the Android App "NFC TagInfo":
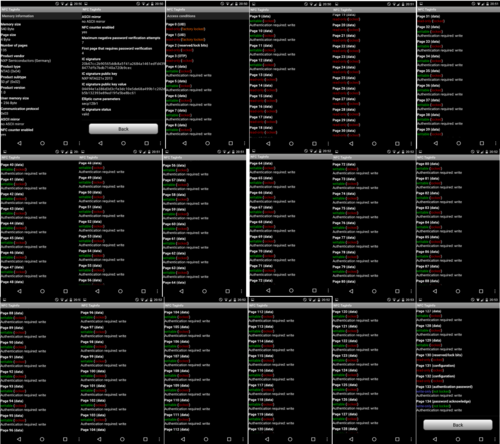
Most of the NFC pages are encrypted. This includes the actual Mii data for the owner, an UTF-16 string for the Amiibo nickname, etc.
The NFC tag for Amiibo is NTAG215.
The NFC 32bit password for the PWD_AUTH command(for enabling write-access to the encrypted NFC pages / etc), appears to be generated from unknown data that doesn't change when the Amiibo data pages are being updated.
The following NTAG215 commands are used when reading an Amiibo:
- GET_VERSION
- READ, startpage=0x03
- PWD_AUTH
- FAST_READ: startpage=0x00, endpage=0x3B
- FAST_READ: startpage=0x3C, endpage=0x77
- FAST_READ: startpage=0x78, endpage=0x86
Therefore, *all* pages from the Amiibo NFC tag are read, including the configuration pages at the end.
Each page is 4-bytes, the following is the structure of the NFC pages:
| NFC page | Total pages | Raw byte offset in EEPROM | Total byte size | Description |
|---|---|---|---|---|
| 0 | 4 | 0x10 | 0x10 | Same as standard NTAG215: 9-byte serial-number, "internal" u8 value, two lock bytes then the "Capability Container (CC)" page. |
| 4 | 8 | 0x10 | 0x20 | SHA256-HMAC over 0x1DF-bytes: first 3-bytes are from the last 3-bytes of page[12], the rest is over the first 0x1DC-bytes of the plaintext data following this hash(see page[13]). |
| 12 | 1 | 0x30 | 0x4 | Unknown. Last 3-bytes here are used with the above HMAC. |
| 13 | 0x34 | The system crypts 0x1A0-bytes starting here. |
Structure of plaintext data from page13
| Offset | Size | Description |
|---|---|---|
| 0x0 | 0xB0 | Amiibo settings are stored within here. |
| 0xB0 | 0xD8 | AppData, for the user-application with the programID specified in the above Amiibo settings. The data stored here is application-specific. |
| 0x188 | 0x18 | Not used in "decrypted" form, since this isn't encrypted to begin with. |
Structure of Amiibo settings
| Offset | Size | Description |
|---|---|---|
| 0x0 | 0x1 | Unknown. The low 4-bits here are copied to the struct used with NFC:GetAmiiboSettings. |
| 0x1 | 0x1 | Unknown. The low 4-bits here are copied to the struct used with NFC:GetAmiiboSettings. |
| 0x2 | 0x2 | ? |
| 0x4 | 0x2 | u16 big-endian, unknown. |
| 0x6 | 0x6 | ? |
| 0xC | 0x14(10*2) | UTF-16BE Amiibo nickname. |
| 0x20 | 0x60 | Owner Mii. |
| 0x80 | 0x8 | Application programID for the AppData, zero otherwise. |
| 0x88 | 0x4 | ? |
| 0x8C | 0x4 | ? |
| 0x90 | 0x20 | Probably a SHA256-HMAC hash. |