游戏存档: Difference between revisions
translate eng.ver www.3dbrew.org/w/index.php?title=Savegames&oldid=7872 |
|||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
本页面描述了 3DS游戏卡, SD/NAND,SD/NAND [[extdata]] 中以及别的地方发现的游戏存档格式,加密方法等等内容。你可以在[[Games|游戏]]页面找到多种游戏的存档。 | |||
=== 加密手段 === | === 加密手段 === | ||
3DS上的游戏存档与DS的很像,都储存在游戏卡带的一块闪存芯片(FLASH chip) | 3DS上的游戏存档与DS的很像,都储存在游戏卡带的一块闪存芯片(FLASH chip)上。DS上这些游戏存档以明文的方式保存,3DS加了一层加密。通过对一些游戏存档的内容进行异或操作,显示出一些明文,看起来存档的加密方式应该是AES-CTR. | ||
( | 这样猜测的理由在于序列密码法曾有一段时间使用512字节(作为单位来加密),即是说,在超过512字节之后,这种加密方法将重复某些关键字序列(keystream)。序列密码法加密的方法是,使用关键字序列对待加密数据进行异或操作,(得到的便是加密数据)。不幸的是,假如你使用重复的关键字序列加密某些已知的明文(在我们的场合里,是数据0),那么你基本上在泄漏你宝贵的关键字序列。(译者注:在位(Bit)级别上进行异或运算时,1^0=1,0^0=0,这里符号"^"表示异或,所以一个数据和0进行异或时会得到它本身。) | ||
那么怎么在3DS上运用这种解密方法呢?首先,将游戏存档切成以512字节为单位长度的片段,然后将除了只包含FF以外的片段以二进制方式查看。现在寻找最常见的公共片段,那就是你的关键字序列。现在用你原始的游戏存档和这些关键字序列进行异或操作,你将得到一个完全解密的游戏存档。对关键字序列进行异或操作以产生加密的游戏存档。(译者注:异或运算的一个重要性质是,a^b^b=a;即使用同样的关键字b对a进行两次异或将得到a本身,所以使用关键字序列对加密的游戏存档异或会得到明文,再异或一次又得到加密的存档。) | |||
==== Savegame keyY ==== | |||
所有的游戏卡和SD卡存储的游戏都是用AES-CTR加密的. The base CTR for gamecard savegames is all-zero. The gamecard savegame [[AES|keyslot]] keyY is unique for every region of each game. The [[NCSD]] partition flags determine the method used to generate this keyY. When the save [[NCSD]] flags checked by the running NATIVE_FIRM are all-zero, the system will use the repeating CTR, otherwise a proper CTR which never repeats within the image is used. When all of the flags checked by the running NATIVE_FIRM are clear, the keyY is a 8-byte block decrypted from the main [[NCCH#CXI|CXI]] + two u32 IDs read from gamecard commands. | |||
===== Hashed keyY and [[2.2.0-4]] Savegame Encryption ===== | |||
( | [[NCSD]] partition的特定标志位被置位时,用CXI数据hash计算一个 SHA-256 (same data used with the original plain keyY), and the 0x40-bytes read from a gamecard command(this 0x40-byte data is also read by [[Process_Services_PXI|GetRomId]]). hash的前0x10-byte用做keyY。当标志位[7]被置位时,CTR不再使用原先的CTR方式使用,在存档镜像中不会使用重复数据。[[2.2.0-4]] 升级后,所有零售版有NCSD的游戏image都被发现在使用这种加密方式。 (含[[2.2.0-4]]以上的[[System Update CFA|System update partition]]), . | ||
This keyY generation method was implemented with [[2.0.0-2]] via NCSD partition flag[3], however the proper CTR wasn't implemented for flag[7] until [[2.2.0-4]]. The hashed keyY flag[3] implemented with [[2.0.0-2]] was likely never used with retail gamecards. | |||
===== [[6.0.0-11]] Savegame keyY ===== | |||
[[6.0.0-11]] implemented support for generating the savegame keyY with a new method, this method is much more complex than previous keyY methods. This is enabled via new [[NCSD]] partition flags, all retail games which have the NCSD image finalized after the [[6.0.0-11]] release(and [[6.0.0-11]]+ in the system update partition) will have these flags set for using this new method. | |||
A SHA-256 hash is calculated over the data used with the above hashed keyY method, other data is hashed here as well. An [[AES]] MAC is then calculated over this hash, the output MAC is used for the savegame keyY. | |||
The keyY used for calculating this AES MAC is initialized while NATIVE_FIRM is loading, this keyY is generated via the [[RSA]] engine. The RSA slot used here is slot0(key-data for slot0 is initialized by bootrom), this RSA slot0 key-data is overwritten once the system boots any [[NCCH#CXI|CXIs]] from NAND like [[NS]]. | |||
=== Wear leveling === | === Wear leveling === | ||
3DS在游戏存档闪存芯片上引入了wear leveling 方案。这是通过使用blockmap和journal来实现的。blockmap在闪存上偏移量为0,其后是journal。初始状态由blockmap指定,然后journal对其进行应用。 | 3DS在游戏存档闪存芯片上引入了wear leveling 方案。这是通过使用blockmap和journal来实现的。blockmap在闪存上偏移量为0,其后是journal。初始状态由blockmap指定,然后journal对其进行应用。 | ||
| Line 51: | Line 47: | ||
blockmap后2字节为最开始的8个字节,以及blockmap的CRC16校验码(开始值为0xFFFF(像modbus))。 | blockmap后2字节为最开始的8个字节,以及blockmap的CRC16校验码(开始值为0xFFFF(像modbus))。 | ||
然后是journal。其结构如下: | 然后是journal。其结构如下: | ||
| Line 73: | Line 68: | ||
</pre> | </pre> | ||
magic 是一个固定值 0x080d6ce0. | |||
blockmap/journal入口的验校和是这样算出的: | |||
* 每个 byte 是一个 0x200 大小加密的块的验校和 | |||
* 计算一个块的CRC16 (从 0xFFFF 开始) ,两个byte的CRC16一起进行异或运算,以产生 8bit 校验和 | |||
=== AES MAC header === | |||
{| class="wikitable" | |||
|- | |||
! Image偏移 | |||
! 长度 | |||
! 说明 | |||
|- | |||
| 0x00 | |||
| 0x10 | |||
| 通过 0x20-byte SHA256 hash的[[AES]]MAC | |||
|- | |||
| 0x10 | |||
| 0xF0 | |||
| 填充0 | |||
|} | |||
这个AES MAC是用于"签名" DISA/DIFF header的. 每次更新游戏存档,存储在DISA/DIFF的hash都会更新.每次更改存档时,必然更新MAC. SHA256_Update()用于使用下面的加密方式计算这个 hash . | |||
==== Savegame Types ==== | |||
{| class="wikitable" | |||
|- | |||
! 类型 | |||
! 说明 | |||
|- | |||
| CTR-EXT0 | |||
| SD/NAND [[Extdata]] | |||
|- | |||
| CTR-SYS0 | |||
| [[System SaveData]] | |||
|- | |||
| CTR-NOR0 | |||
| 卡带游戏存档 | |||
|- | |||
| CTR-SAV0 | |||
| 游戏存档 | |||
|- | |||
| CTR-SIGN | |||
| SD卡游戏存档 | |||
|- | |||
| CTR-9DB0 | |||
| [[Title_Database|Title database]] extdata images | |||
|} | |||
==== Extdata SHA256 Blocks ==== | |||
{| class="wikitable" | |||
|- | |||
! 块的长度 | |||
! 说明 | |||
|- | |||
| 0x8 | |||
| 游戏存档类型 | |||
|- | |||
| 0x8 | |||
| First word is the hex ID from image filename, second word is the hex ID of the sub-dir under the <ExtdataIDLow> directory (all-zero for Quota.dat) | |||
|- | |||
| 0x4 | |||
| 1 for Quota.dat, 0 otherwise | |||
|- | |||
| 0x8 | |||
| Same as the previous u64 | |||
|- | |||
| 0x100 | |||
| DIFF header | |||
|} | |||
==== System SaveData SHA256 Blocks ==== | |||
{| class="wikitable" | |||
|- | |||
! Block Size | |||
! Description | |||
|- | |||
| 0x8 | |||
| Savegame type | |||
|- | |||
| 0x8 | |||
| [[FS:OpenFile|SaveID]] | |||
|- | |||
| 0x100 | |||
| DISA header | |||
|} | |||
==== CTR-NOR0 SHA256 Blocks ==== | |||
{| class="wikitable" | |||
|- | |||
! Block Size | |||
! Description | |||
|- | |||
| 0x8 | |||
| Savegame type | |||
|- | |||
| 0x100 | |||
| DISA header | |||
|} | |||
==== CTR-SAV0 SHA256 Blocks ==== | |||
{| class="wikitable" | |||
|- | |||
! Block Size | |||
! Description | |||
|- | |||
| 0x8 | |||
| Savegame type | |||
|- | |||
| | |||
| Input data, for gamecard savegames this is the output SHA-256 hash from CTR-NOR0. | |||
|} | |||
For gamecard savegames the output hash from this is used with the MAC. This save-type is also used for SD savegames, for SD saves the input data is the 0x100-byte DISA header. For SD savegames, the calculated output hash is used with CTR-SIGN. | |||
==== CTR-SIGN SHA256 Blocks ==== | |||
{| class="wikitable" | |||
|- | |||
! Block Size | |||
! Description | |||
|- | |||
| 0x8 | |||
| Savegame type | |||
|- | |||
| 0x8 | |||
| ProgramID/SaveID | |||
|- | |||
| 0x20 | |||
| SHA-256 hash from CTR-SAV0 | |||
|} | |||
This is used for SD savegames, the calculated hash from this is used with the MAC. | |||
==== CTR-9DB0 SHA256 Blocks ==== | |||
{| class="wikitable" | |||
|- | |||
! Block Size | |||
! Description | |||
|- | |||
| 0x8 | |||
| Savegame type | |||
|- | |||
| 0x4 | |||
| ID, each .db image has a separate ID. | |||
|- | |||
| 0x100 | |||
| DIFF header | |||
|} | |||
This is used for the /[[Title_Database|dbs]] .db extdata images. | |||
=== Partitions === | === Partitions === | ||
There can be multiple partitions | There can be multiple partitions in the image. | ||
The partitions are represented by tables of DIFI blobs inside a DISA structure. | The partitions are represented by tables of DIFI blobs inside a DISA/DIFF structure. | ||
The order of the DIFI blobs is the order of the partitions in the | The order of the DIFI blobs is the order of the partitions in the image. | ||
==== DISA ==== | |||
* If the uint32 @ | * This is located @ 0x100 in the image, following the MAC header. | ||
* If the uint32 @ 0x68 in the DISA(the low 8-bits) is non-zero, then the secondary table is is used, otherwise the primary table is used. | |||
* If the table has more then 1 DIFI then the uint32 @ 0x168 is the offset from the DATA partition to the file base (masked with 0xFFFFFFFE). | * If the table has more then 1 DIFI then the uint32 @ 0x168 is the offset from the DATA partition to the file base (masked with 0xFFFFFFFE). | ||
{| class="wikitable" | {| class="wikitable" | ||
| Line 107: | Line 249: | ||
| 0x08 | | 0x08 | ||
| 8 | | 8 | ||
| | | Total partition entries in a table | ||
|- | |- | ||
| 0x10 | | 0x10 | ||
| 8 | | 8 | ||
| Offset to | | Offset to secondary partition table | ||
|- | |- | ||
| 0x18 | | 0x18 | ||
| 8 | | 8 | ||
| Offset to | | Offset to primary partition table | ||
|- | |- | ||
| 0x20 | | 0x20 | ||
| 8 | | 8 | ||
| Partition table | | Partition table size | ||
|- | |- | ||
| 0x28 | | 0x28 | ||
| Line 162: | Line 304: | ||
|- | |- | ||
| 0x8C | | 0x8C | ||
| | | 0x74 | ||
| | | Reserved | ||
|} | |} | ||
* The hash in the DISA hashes the Active Table (starting from tables's offset to tables's offset + table length) with SHA256. | * The hash in the DISA hashes the Active Table (starting from tables's offset to tables's offset + table length) with SHA256. | ||
* The partition offsets are absolute offsets in the image. | |||
* The SAVE partition offset is usually 0x1000. The SAVE/DATA partitions begins with the DPFS partitions, the relative offset for the IVFC partition data is specified by the DPFS header. | |||
The DIFIs table at offset 0x200 in the image has 2 DIFIs when the DATA partition isn't used, 4 DIFIs otherwise. Each partition table contains the SAVE DIFI entry and optionally the DATA entry. The secondary partition table is located at offset 0x200 in the image, and the primary table follows the secondary table. | |||
The | The non-active table is for backup. | ||
==== DIFF ==== | |||
* This is the [[extdata]] equivalent of DISA, for extdata which use FS. DIFF is only used for extdata. | |||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| Line 196: | Line 335: | ||
| 0x08 | | 0x08 | ||
| 8 | | 8 | ||
| | | Secondary partition table offset | ||
|- | |- | ||
| 0x10 | | 0x10 | ||
| 8 | | 8 | ||
| | | Primary partition table offset | ||
|- | |- | ||
| 0x18 | | 0x18 | ||
| Line 207: | Line 346: | ||
|- | |- | ||
| 0x20 | | 0x20 | ||
| 8 | |||
| File Base Offset | |||
|- | |||
| 0x28 | |||
| 8 | |||
| File Base Size | |||
|- | |||
| 0x30 | |||
| 4 | | 4 | ||
| Active | | Active Partition Table (0 = Primary, 1 = Secondary) | ||
|- | |- | ||
| 0x34 | | 0x34 | ||
| 0x20 | | 0x20 | ||
| Hash of the | | Hash of the Active Partition Table | ||
|- | |- | ||
| 0x54 | | 0x54 | ||
| | | 0xAC | ||
| | | Reserved1 | ||
|} | |} | ||
==== DIFI ==== | |||
These | These 0x12C-byte blobs describe the partitions. Following each partition is an unused 0xFFFFFFFF cleartext word in the raw image. Every DIFI blob describes a partition. Partitions are catted together, so after the end of one partition is the beginning of the next. | ||
For most games there's only 1 partition (The SAVE partition) and some (like Asphalt 3D, Steel Diver & Lego Star Wars III) has 2 partitions. | For most games there's only 1 partition (The SAVE partition) and some (like Asphalt 3D, Steel Diver & Lego Star Wars III) has 2 partitions. | ||
* 2 Partitions means that the files inside the SAVE partition is on the | * 2 Partitions means that the files inside the SAVE partition is on the DATA partition. | ||
* The DISA/DIFF headers support a maximum of 2 partitions. | |||
* | |||
{| class="wikitable" | {| class="wikitable" | ||
| Line 251: | Line 391: | ||
| 0x08 | | 0x08 | ||
| 8 | | 8 | ||
| Offset to "IVFC" blob in DIFI ( | | Offset to "IVFC" blob in DIFI (Always 0x44) | ||
|- | |- | ||
| 0x10 | | 0x10 | ||
| Line 259: | Line 399: | ||
| 0x18 | | 0x18 | ||
| 8 | | 8 | ||
| Offset to "DPFS" blob in DIFI ( | | Offset to "DPFS" blob in DIFI (Always 0xBC) | ||
|- | |- | ||
| 0x20 | | 0x20 | ||
| Line 267: | Line 407: | ||
| 0x28 | | 0x28 | ||
| 8 | | 8 | ||
| Offset to the hash in DIFI ( | | Offset to the hash in DIFI (Always 0x10C) | ||
|- | |- | ||
| 0x30 | | 0x30 | ||
| Line 282: | Line 422: | ||
|} | |} | ||
==== IVFC ==== | |||
{| class="wikitable" | {| class="wikitable" | ||
| Line 299: | Line 439: | ||
|- | |- | ||
| 0x08 | | 0x08 | ||
| | | 0x8 | ||
| | | Master hash size | ||
|- | |- | ||
| 0x10 | | 0x10 | ||
| | | 0x8 | ||
| | | Level 1 relative offset | ||
|- | |- | ||
| 0x18 | | 0x18 | ||
| | | 0x8 | ||
| | | Level 1 hashdata size | ||
|- | |- | ||
| 0x20 | | 0x20 | ||
| | | 0x4 | ||
| | | Level 1 block size, in log2 | ||
|- | |||
| 0x24 | |||
| 0x4 | |||
| Reserved | |||
|- | |- | ||
| 0x28 | | 0x28 | ||
| | | 0x8 | ||
| | | Level 2 relative offset | ||
|- | |- | ||
| 0x30 | | 0x30 | ||
| | | 0x8 | ||
| | | Level 2 hashdata size | ||
|- | |- | ||
| 0x38 | | 0x38 | ||
| | | 0x4 | ||
| | | Level 2 block size, in log2. | ||
|- | |||
| 0x3C | |||
| 0x4 | |||
| Reserved | |||
|- | |- | ||
| 0x40 | | 0x40 | ||
| | | 0x8 | ||
| | | Level 3 relative offset | ||
|- | |- | ||
| 0x48 | | 0x48 | ||
| | | 0x8 | ||
| | | Level 3 hashdata size | ||
|- | |- | ||
| 0x50 | | 0x50 | ||
| | | 0x4 | ||
| | | Level 3 block size, in log2. | ||
|- | |||
| 0x54 | |||
| 0x4 | |||
| Reserved | |||
|- | |- | ||
| 0x58 | | 0x58 | ||
| 8 | | 8 | ||
| | | Level 4 filesystem relative offset | ||
|- | |- | ||
| 0x60 | | 0x60 | ||
| 8 | | 8 | ||
| | | Level 4 filesystem size | ||
|- | |- | ||
| 0x68 | | 0x68 | ||
| 8 | | 8 | ||
| | | Level 4 filesystem block size, in log2. | ||
|- | |- | ||
| 0x70 | | 0x70 | ||
| Line 356: | Line 508: | ||
|} | |} | ||
* | * This savegame IVFC is almost identical to the [[RomFS]] IVFC, except for the additional filesystem level. Exactly like RomFS, each level except level4 is a hash-table where each hash entry hashes the data in the next level, padded to the log2 block size. | ||
==== DPFS ==== | |||
{| class="wikitable" | {| class="wikitable" | ||
| Line 376: | Line 528: | ||
| 0x08 | | 0x08 | ||
| 8 | | 8 | ||
| Offset | | Offset to first table | ||
|- | |- | ||
| 0x10 | | 0x10 | ||
| Line 388: | Line 540: | ||
| 0x20 | | 0x20 | ||
| 8 | | 8 | ||
| Offset | | Offset to second table | ||
|- | |- | ||
| 0x28 | | 0x28 | ||
| Line 400: | Line 552: | ||
| 0x38 | | 0x38 | ||
| 8 | | 8 | ||
| | | IVFC partition offset | ||
|- | |- | ||
| 0x40 | | 0x40 | ||
| 8 | | 8 | ||
| | | IVFC partition size | ||
|- | |- | ||
| 0x48 | | 0x48 | ||
| 8 | | 8 | ||
| | | IVFC partition block size (1<<value) | ||
|- | |- | ||
|} | |} | ||
* Every block this table point to is written twice (concatenated). You can see that the offset to the next block is twice the length (except the data which always begin after 0x1000). | * Every block this table point to is written twice (concatenated). You can see that the offset to the next block is twice the length (except the data which always begin after 0x1000). | ||
* The offsets contained in the DPFS and IVFC are relative to the partition offset in the DISA/DIFF. The offsets from the IVFC are additionally added with the IVFC partition offset from the DPFS. | |||
The first partition's data starts at 0x2000. First comes the hashtable (usually start @ 0x40 into the partition) and then the filesystem. | The first partition's data usually starts at 0x2000. First comes the hashtable (usually start @ 0x40 into the partition) and then the filesystem. | ||
The hashtable entries' size is 2^x where x is the ' | The hashtable entries' size is 2^x where x is the 'Filesystem block size' from the IVFC block. | ||
'''Hash''' | '''DIFI Hash''' | ||
The last 0x20-bytes of the partition following the DIFI, IVFC and DPFS is a SHA256 hash. The offset to this hash is stored in the DIFI. This hashes the IVFC level 1, with the buffer which is hashed aligned to the IVFC level 1 log2 block-size. | |||
'''Summary Drawing''' | '''Summary Drawing''' | ||
| Line 482: | Line 635: | ||
00002620: 00000000 00000000 00000000 00000000 ................ | 00002620: 00000000 00000000 00000000 00000000 ................ | ||
00002630: 01000000 73797374 656D2E64 61740000 ....system.dat.. | 00002630: 01000000 73797374 656D2E64 61740000 ....system.dat.. | ||
00002640: 00000000 00000000 D57B1100 02000000 ........ | 00002640: 00000000 00000000 D57B1100 02000000 ........?{...... | ||
00002650: 22000000 00000000 E8121500 00000000 ".......è....... | 00002650: 22000000 00000000 E8121500 00000000 ".......è....... | ||
00002660: 01000000 73617665 30302E62 696E0000 ....save00.bin.. | 00002660: 01000000 73617665 30302E62 696E0000 ....save00.bin.. | ||
00002670: 00000000 01000000 69921100 03000000 ........i’...... | 00002670: 00000000 01000000 69921100 03000000 ........i’...... | ||
00002680: DC140000 00000000 04000000 00000000 | 00002680: DC140000 00000000 04000000 00000000 ü............... | ||
</pre> | </pre> | ||
| Line 521: | Line 674: | ||
| 0x24 | | 0x24 | ||
| 4 | | 4 | ||
| | | Media-size for the below sections | ||
|- | |- | ||
| 0x28 | | 0x28 | ||
| Line 533: | Line 686: | ||
| 0x34 | | 0x34 | ||
| 4 | | 4 | ||
| FolderMap | | Unknown, FolderMap size-related | ||
|- | |- | ||
| 0x38 | | 0x38 | ||
| Line 545: | Line 698: | ||
| 0x44 | | 0x44 | ||
| 4 | | 4 | ||
| FileMap | | Unknown, FileMap size-related | ||
|- | |- | ||
| 0x48 | | 0x48 | ||
| Line 557: | Line 710: | ||
| 0x54 | | 0x54 | ||
| 4 | | 4 | ||
| BlockMap | | Uknown, BlockMap size-related | ||
|- | |- | ||
| 0x58 | | 0x58 | ||
| Line 569: | Line 722: | ||
| 0x64 | | 0x64 | ||
| 4 | | 4 | ||
| File store | | Unknown, File store size-related | ||
|- | |- | ||
| 0x68 | | 0x68 | ||
| Line 585: | Line 738: | ||
| 0x74 | | 0x74 | ||
| 4 | | 4 | ||
| Folders Table | | Unknown, Folders Table size-related | ||
|- | |- | ||
| 0x78 | | 0x78 | ||
| Line 601: | Line 754: | ||
| 0x84 | | 0x84 | ||
| 4 | | 4 | ||
| Files Table | | Unknown, Files Table size-related | ||
|- | |- | ||
|} | |} | ||
| Line 612: | Line 765: | ||
[[File:Sfsave_drawing.png]] | [[File:Sfsave_drawing.png]] | ||
=== | === 初始化 === | ||
When a save FLASH contains all xFFFF blocks it's assumed uninitialized by the game cartridges and it initializes default data in place, without prompting the user. | 当一个存储FLASH包含所有xFFFF块,它假定由游戏墨盒未初始化,初始化默认数据的地方,不提示用户的情况下。0xFFFFFFFF的块未初始化的数据。当创建一个非游戏卡的秘技和其他图像/文件,它的最初所有0xFFFFFFFF的,直到它的一些块格式化,加密数据覆盖。 | ||
When a save FLASH contains all xFFFF blocks it's assumed uninitialized by the game cartridges and it initializes default data in place, without prompting the user. The 0xFFFFFFFF blocks are uninitialized data. When creating a non-gamecard savegame and other images/files, it's initially all 0xFFFFFFFF until it's formatted where some of the blocks are overwritten with encrypted data. | |||
我得到了一个新的游戏 SplinterCell3D-Pal ,它的128KB存档除去开头的0x10 byte是‘Z’(大写),其余都为0xFF --[[User:Elisherer|Elisherer]] 22:41 2011年10月15日(CEST) | |||
=== | === 事实 === | ||
如果你发现二进制文件的一些事实把它们分享到这里: | |||
* | * 从一个存档到这个游戏在这个分区的另一个游戏备份,后者全部image的头部变为随机位置.. --[[User:Elisherer|Elisherer]] 22:41 2011年10月15日(CEST) | ||
从一个“随机”位置在分区和整个图像头的最后一个文件,保存到另一个游戏备份.. | |||
=== 工具 === | |||
* [https://github.com/3dshax/3ds/tree/master/3dsfuse 3dsfuse] 支持读写游戏存档。在mount的FUSE文件系统中,/output.sav是raw FLASH save-image。When the save was modified, a separate tool to update the MAC must be used with /clean.sav, prior to writing output.sav to a gamecard. | |||
* [[3DSExplorer]] supports reading of savegames, it doesn't support reading the new encrypted savegames and maybe in the future it will support modifying (some of the modyfing code is already implemented). | |||
[[セーブデータ|Japanese]] | [[セーブデータ|Japanese]] | ||
Latest revision as of 15:38, 24 August 2013
本页面描述了 3DS游戏卡, SD/NAND,SD/NAND extdata 中以及别的地方发现的游戏存档格式,加密方法等等内容。你可以在游戏页面找到多种游戏的存档。
加密手段
3DS上的游戏存档与DS的很像,都储存在游戏卡带的一块闪存芯片(FLASH chip)上。DS上这些游戏存档以明文的方式保存,3DS加了一层加密。通过对一些游戏存档的内容进行异或操作,显示出一些明文,看起来存档的加密方式应该是AES-CTR.
这样猜测的理由在于序列密码法曾有一段时间使用512字节(作为单位来加密),即是说,在超过512字节之后,这种加密方法将重复某些关键字序列(keystream)。序列密码法加密的方法是,使用关键字序列对待加密数据进行异或操作,(得到的便是加密数据)。不幸的是,假如你使用重复的关键字序列加密某些已知的明文(在我们的场合里,是数据0),那么你基本上在泄漏你宝贵的关键字序列。(译者注:在位(Bit)级别上进行异或运算时,1^0=1,0^0=0,这里符号"^"表示异或,所以一个数据和0进行异或时会得到它本身。)
那么怎么在3DS上运用这种解密方法呢?首先,将游戏存档切成以512字节为单位长度的片段,然后将除了只包含FF以外的片段以二进制方式查看。现在寻找最常见的公共片段,那就是你的关键字序列。现在用你原始的游戏存档和这些关键字序列进行异或操作,你将得到一个完全解密的游戏存档。对关键字序列进行异或操作以产生加密的游戏存档。(译者注:异或运算的一个重要性质是,a^b^b=a;即使用同样的关键字b对a进行两次异或将得到a本身,所以使用关键字序列对加密的游戏存档异或会得到明文,再异或一次又得到加密的存档。)
Savegame keyY
所有的游戏卡和SD卡存储的游戏都是用AES-CTR加密的. The base CTR for gamecard savegames is all-zero. The gamecard savegame keyslot keyY is unique for every region of each game. The NCSD partition flags determine the method used to generate this keyY. When the save NCSD flags checked by the running NATIVE_FIRM are all-zero, the system will use the repeating CTR, otherwise a proper CTR which never repeats within the image is used. When all of the flags checked by the running NATIVE_FIRM are clear, the keyY is a 8-byte block decrypted from the main CXI + two u32 IDs read from gamecard commands.
Hashed keyY and 2.2.0-4 Savegame Encryption
NCSD partition的特定标志位被置位时,用CXI数据hash计算一个 SHA-256 (same data used with the original plain keyY), and the 0x40-bytes read from a gamecard command(this 0x40-byte data is also read by GetRomId). hash的前0x10-byte用做keyY。当标志位[7]被置位时,CTR不再使用原先的CTR方式使用,在存档镜像中不会使用重复数据。2.2.0-4 升级后,所有零售版有NCSD的游戏image都被发现在使用这种加密方式。 (含2.2.0-4以上的System update partition), .
This keyY generation method was implemented with 2.0.0-2 via NCSD partition flag[3], however the proper CTR wasn't implemented for flag[7] until 2.2.0-4. The hashed keyY flag[3] implemented with 2.0.0-2 was likely never used with retail gamecards.
6.0.0-11 Savegame keyY
6.0.0-11 implemented support for generating the savegame keyY with a new method, this method is much more complex than previous keyY methods. This is enabled via new NCSD partition flags, all retail games which have the NCSD image finalized after the 6.0.0-11 release(and 6.0.0-11+ in the system update partition) will have these flags set for using this new method.
A SHA-256 hash is calculated over the data used with the above hashed keyY method, other data is hashed here as well. An AES MAC is then calculated over this hash, the output MAC is used for the savegame keyY.
The keyY used for calculating this AES MAC is initialized while NATIVE_FIRM is loading, this keyY is generated via the RSA engine. The RSA slot used here is slot0(key-data for slot0 is initialized by bootrom), this RSA slot0 key-data is overwritten once the system boots any CXIs from NAND like NS.
Wear leveling
3DS在游戏存档闪存芯片上引入了wear leveling 方案。这是通过使用blockmap和journal来实现的。blockmap在闪存上偏移量为0,其后是journal。初始状态由blockmap指定,然后journal对其进行应用。
The 3DS employs a wear leveling scheme on the savegame FLASH chips. This is done through the usage of blockmaps and a journal. The blockmap is located at offset 0 of the flash chip, and is immediately followed by the journal. The initial state is dictated by the blockmap, and the journal is then applied to that.
首先,是8字节目前还不明白其确切意义的数据。然后是实际的blockmap。其结构很简单:
struct header_entry {
uint8_t phys_sec; // when bit7 is set, block has checksums, otherwise checksums are all zero
uint8_t alloc_cnt;
uint8_t chksums[8];
} __attribute__((__packed__));
每个sector有一个入口,从实际的sector1开始计数(sector 0 包含blockmap/journal)。
blockmap后2字节为最开始的8个字节,以及blockmap的CRC16校验码(开始值为0xFFFF(像modbus))。
然后是journal。其结构如下:
struct sector_entry {
uint8_t virt_sec; // Mapped to sector
uint8_t prev_virt_sec; // Physical sector previously mapped to
uint8_t phys_sec; // Mapped from sector
uint8_t prev_phys_sec; // Virtual sector previously mapped to
uint8_t phys_realloc_cnt; // Amount of times physical sector has been remapped
uint8_t virt_realloc_cnt; // Amount of times virtual sector has been remapped
uint8_t chksums[8];
} __attribute__((__packed__));
struct long_sector_entry{
struct sector_entry sector;
struct sector_entry dupe;
uint32_t magic;
}__attribute__((__packed__));
magic 是一个固定值 0x080d6ce0.
blockmap/journal入口的验校和是这样算出的:
- 每个 byte 是一个 0x200 大小加密的块的验校和
- 计算一个块的CRC16 (从 0xFFFF 开始) ,两个byte的CRC16一起进行异或运算,以产生 8bit 校验和
AES MAC header
| Image偏移 | 长度 | 说明 |
|---|---|---|
| 0x00 | 0x10 | 通过 0x20-byte SHA256 hash的AESMAC |
| 0x10 | 0xF0 | 填充0 |
这个AES MAC是用于"签名" DISA/DIFF header的. 每次更新游戏存档,存储在DISA/DIFF的hash都会更新.每次更改存档时,必然更新MAC. SHA256_Update()用于使用下面的加密方式计算这个 hash .
Savegame Types
| 类型 | 说明 |
|---|---|
| CTR-EXT0 | SD/NAND Extdata |
| CTR-SYS0 | System SaveData |
| CTR-NOR0 | 卡带游戏存档 |
| CTR-SAV0 | 游戏存档 |
| CTR-SIGN | SD卡游戏存档 |
| CTR-9DB0 | Title database extdata images |
Extdata SHA256 Blocks
| 块的长度 | 说明 |
|---|---|
| 0x8 | 游戏存档类型 |
| 0x8 | First word is the hex ID from image filename, second word is the hex ID of the sub-dir under the <ExtdataIDLow> directory (all-zero for Quota.dat) |
| 0x4 | 1 for Quota.dat, 0 otherwise |
| 0x8 | Same as the previous u64 |
| 0x100 | DIFF header |
System SaveData SHA256 Blocks
| Block Size | Description |
|---|---|
| 0x8 | Savegame type |
| 0x8 | SaveID |
| 0x100 | DISA header |
CTR-NOR0 SHA256 Blocks
| Block Size | Description |
|---|---|
| 0x8 | Savegame type |
| 0x100 | DISA header |
CTR-SAV0 SHA256 Blocks
| Block Size | Description |
|---|---|
| 0x8 | Savegame type |
| Input data, for gamecard savegames this is the output SHA-256 hash from CTR-NOR0. |
For gamecard savegames the output hash from this is used with the MAC. This save-type is also used for SD savegames, for SD saves the input data is the 0x100-byte DISA header. For SD savegames, the calculated output hash is used with CTR-SIGN.
CTR-SIGN SHA256 Blocks
| Block Size | Description |
|---|---|
| 0x8 | Savegame type |
| 0x8 | ProgramID/SaveID |
| 0x20 | SHA-256 hash from CTR-SAV0 |
This is used for SD savegames, the calculated hash from this is used with the MAC.
CTR-9DB0 SHA256 Blocks
| Block Size | Description |
|---|---|
| 0x8 | Savegame type |
| 0x4 | ID, each .db image has a separate ID. |
| 0x100 | DIFF header |
This is used for the /dbs .db extdata images.
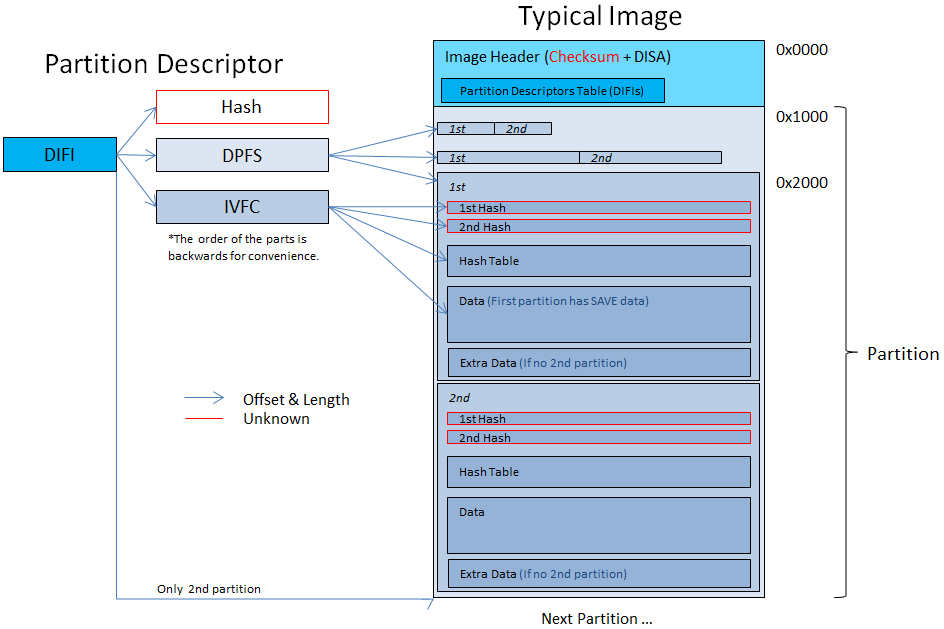
Partitions
There can be multiple partitions in the image. The partitions are represented by tables of DIFI blobs inside a DISA/DIFF structure. The order of the DIFI blobs is the order of the partitions in the image.
DISA
- This is located @ 0x100 in the image, following the MAC header.
- If the uint32 @ 0x68 in the DISA(the low 8-bits) is non-zero, then the secondary table is is used, otherwise the primary table is used.
- If the table has more then 1 DIFI then the uint32 @ 0x168 is the offset from the DATA partition to the file base (masked with 0xFFFFFFFE).
| Start | Length | Description |
|---|---|---|
| 0x00 | 4 | Magic ("DISA") |
| 0x04 | 4 | Magic Number (0x40000) |
| 0x08 | 8 | Total partition entries in a table |
| 0x10 | 8 | Offset to secondary partition table |
| 0x18 | 8 | Offset to primary partition table |
| 0x20 | 8 | Partition table size |
| 0x28 | 8 | SAVE Partition entry offset in the partition table |
| 0x30 | 8 | SAVE Partition entry length in the partition table |
| 0x38 | 8 | DATA Partition entry offset in the partition table |
| 0x40 | 8 | DATA Partition entry length in the partition table |
| 0x48 | 8 | SAVE Partition offset |
| 0x50 | 8 | SAVE Partition length |
| 0x58 | 8 | DATA Partition offset |
| 0x60 | 8 | DATA Partition length |
| 0x68 | 4 | Active table (and the offset to the filebase) |
| 0x6C | 0x20 | Hash from active table |
| 0x8C | 0x74 | Reserved |
- The hash in the DISA hashes the Active Table (starting from tables's offset to tables's offset + table length) with SHA256.
- The partition offsets are absolute offsets in the image.
- The SAVE partition offset is usually 0x1000. The SAVE/DATA partitions begins with the DPFS partitions, the relative offset for the IVFC partition data is specified by the DPFS header.
The DIFIs table at offset 0x200 in the image has 2 DIFIs when the DATA partition isn't used, 4 DIFIs otherwise. Each partition table contains the SAVE DIFI entry and optionally the DATA entry. The secondary partition table is located at offset 0x200 in the image, and the primary table follows the secondary table.
The non-active table is for backup.
DIFF
- This is the extdata equivalent of DISA, for extdata which use FS. DIFF is only used for extdata.
| Start | Length | Description |
|---|---|---|
| 0x00 | 4 | Magic ("DIFF") |
| 0x04 | 4 | Magic Number (0x30000) |
| 0x08 | 8 | Secondary partition table offset |
| 0x10 | 8 | Primary partition table offset |
| 0x18 | 8 | Partition table length |
| 0x20 | 8 | File Base Offset |
| 0x28 | 8 | File Base Size |
| 0x30 | 4 | Active Partition Table (0 = Primary, 1 = Secondary) |
| 0x34 | 0x20 | Hash of the Active Partition Table |
| 0x54 | 0xAC | Reserved1 |
DIFI
These 0x12C-byte blobs describe the partitions. Following each partition is an unused 0xFFFFFFFF cleartext word in the raw image. Every DIFI blob describes a partition. Partitions are catted together, so after the end of one partition is the beginning of the next.
For most games there's only 1 partition (The SAVE partition) and some (like Asphalt 3D, Steel Diver & Lego Star Wars III) has 2 partitions.
- 2 Partitions means that the files inside the SAVE partition is on the DATA partition.
- The DISA/DIFF headers support a maximum of 2 partitions.
| Start | Length | Description |
|---|---|---|
| 0x00 | 4 | Magic ("DIFI") |
| 0x04 | 4 | Magic Number (0x10000) |
| 0x08 | 8 | Offset to "IVFC" blob in DIFI (Always 0x44) |
| 0x10 | 8 | Size of "IVFC" blob |
| 0x18 | 8 | Offset to "DPFS" blob in DIFI (Always 0xBC) |
| 0x20 | 8 | Size of "DPFS" blob |
| 0x28 | 8 | Offset to the hash in DIFI (Always 0x10C) |
| 0x30 | 8 | Size of this hash |
| 0x38 | 4 | Flags (when this byte is non-zero, this is a DATA partition) |
| 0x3C | 8 | File base offset (for DATA partitions) |
IVFC
| Start | Length | Description |
|---|---|---|
| 0x00 | 4 | Magic ("IVFC") |
| 0x04 | 4 | Magic Number (0x20000) |
| 0x08 | 0x8 | Master hash size |
| 0x10 | 0x8 | Level 1 relative offset |
| 0x18 | 0x8 | Level 1 hashdata size |
| 0x20 | 0x4 | Level 1 block size, in log2 |
| 0x24 | 0x4 | Reserved |
| 0x28 | 0x8 | Level 2 relative offset |
| 0x30 | 0x8 | Level 2 hashdata size |
| 0x38 | 0x4 | Level 2 block size, in log2. |
| 0x3C | 0x4 | Reserved |
| 0x40 | 0x8 | Level 3 relative offset |
| 0x48 | 0x8 | Level 3 hashdata size |
| 0x50 | 0x4 | Level 3 block size, in log2. |
| 0x54 | 0x4 | Reserved |
| 0x58 | 8 | Level 4 filesystem relative offset |
| 0x60 | 8 | Level 4 filesystem size |
| 0x68 | 8 | Level 4 filesystem block size, in log2. |
| 0x70 | 8 | Unknown (usually 0x78=120) |
- This savegame IVFC is almost identical to the RomFS IVFC, except for the additional filesystem level. Exactly like RomFS, each level except level4 is a hash-table where each hash entry hashes the data in the next level, padded to the log2 block size.
DPFS
| Start | Length | Description |
|---|---|---|
| 0x00 | 4 | Magic ("DPFS") |
| 0x04 | 4 | Magic Number (0x10000) |
| 0x08 | 8 | Offset to first table |
| 0x10 | 8 | First table length |
| 0x18 | 8 | First table block size (1<<value) |
| 0x20 | 8 | Offset to second table |
| 0x28 | 8 | Second table length |
| 0x30 | 8 | Second table block size (1<<value) |
| 0x38 | 8 | IVFC partition offset |
| 0x40 | 8 | IVFC partition size |
| 0x48 | 8 | IVFC partition block size (1<<value) |
- Every block this table point to is written twice (concatenated). You can see that the offset to the next block is twice the length (except the data which always begin after 0x1000).
- The offsets contained in the DPFS and IVFC are relative to the partition offset in the DISA/DIFF. The offsets from the IVFC are additionally added with the IVFC partition offset from the DPFS.
The first partition's data usually starts at 0x2000. First comes the hashtable (usually start @ 0x40 into the partition) and then the filesystem.
The hashtable entries' size is 2^x where x is the 'Filesystem block size' from the IVFC block.
DIFI Hash
The last 0x20-bytes of the partition following the DIFI, IVFC and DPFS is a SHA256 hash. The offset to this hash is stored in the DIFI. This hashes the IVFC level 1, with the buffer which is hashed aligned to the IVFC level 1 log2 block-size.
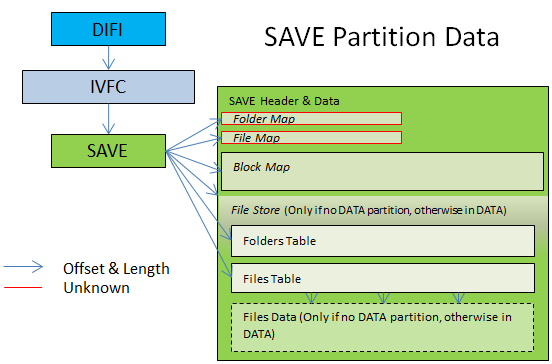
Summary Drawing
The SAVE partition
- The SAVE filesystem works with a backup. There are two SAVE blocks inside the partition concatenated. Which SAVE block is the updated one is unknown yet.. (I'm guessing from experience that (image[0x100B] & 0x20) == 0x20 --> 1st SAVE --Elisherer 01:30, 18 October 2011 (CEST))
Finding the folders table:
- If DATA partition exists: At folder table exact offset from the SAVE struct (from the beginning of the struct).
- Otherwise: The 'folder table offset' * 'folder table media' (=0x200) from the 'filestore offset'. (usually 0 from filebase)
Finding the files table:
- If DATA partition exists: At file table exact offset from the SAVE struct (from the beginning of the struct).
- Otherwise: The 'file table offset' * 'file table media' (=0x200) from the 'filestore offset'.
Detemining the filestore base:
- If DATA partition exists: At file base from the DATA's DIFI struct into the DATA partition.
- Otherwise: At the 'filestore offset' from the beginning of the SAVE struct.
Folder's entry structure:
struct folder_entry {
u32 parent_folder_index;
u8 filename[0x10];
u32 folder_index;
u32 unk1;
u32 last_file_index;
u32 unk3;
u32 unk4;
}
File's entry structure:
struct file_entry {
u32 parent_folder_index;
u8 filename[0x10];
u32 index;
u32 unk1; // magic?
u32 block_offset;
u64 file_size;
u32 unk2; // flags?
u32 unk3;
}
The first entry in both tables is the count of the table, the parent directory index will be the amount of table rows. The root includes itself, so there are the amount - 1 (minus one) folders in the root directory (or files). The entries that follow after the root are the actual folders/files.
Reading the files out is as simple as taking the file base offset and adding (block_offset * 0x200) to it.
Here's a follow-up example from the Legend of Zelda: Ocarina of Time 3D:
//FST entry = SAVE base + File base + (FST offset * 0x200) + (FST entry # * 0x30)
//0x2600 = 0x2000 + 0x400 + (0x1 * 0x200) + (0x0 * 0x30)
00002600: 03000000 09000000 00000000 00000000 ................
00002610: 00000000 00000000 00000000 00000000 ................
00002620: 00000000 00000000 00000000 00000000 ................
00002630: 01000000 73797374 656D2E64 61740000 ....system.dat..
00002640: 00000000 00000000 D57B1100 02000000 ........?{......
00002650: 22000000 00000000 E8121500 00000000 ".......è.......
00002660: 01000000 73617665 30302E62 696E0000 ....save00.bin..
00002670: 00000000 01000000 69921100 03000000 ........i’......
00002680: DC140000 00000000 04000000 00000000 ü...............
| Start | Length | Description |
|---|---|---|
| 0x00 | 4 | Magic ("SAVE") |
| 0x04 | 4 | Magic Number (0x40000) |
| 0x08 | 8 | Offset to data in this SAVE header(normally 0x20) |
| 0x10 | 8 | Partition Size [medias] |
| 0x18 | 4 | Partition Media Size |
| 0x1C | 8 | Unknown |
| 0x24 | 4 | Media-size for the below sections |
| 0x28 | 8 | FolderMap Offset |
| 0x30 | 4 | FolderMap Size |
| 0x34 | 4 | Unknown, FolderMap size-related |
| 0x38 | 8 | FileMap Offset |
| 0x40 | 4 | FileMap Size |
| 0x44 | 4 | Unknown, FileMap size-related |
| 0x48 | 8 | BlockMap Offset |
| 0x50 | 4 | BlockMap Size |
| 0x54 | 4 | Uknown, BlockMap size-related |
| 0x58 | 8 | File store offset (from SAVE) |
| 0x60 | 4 | File store length [medias] |
| 0x64 | 4 | Unknown, File store size-related |
| 0x68 | 4/8 | Folders Table offset (8 bytes in DATA) |
| 0x6C | 4 | Folders Table Length (medias) (Only in no DATA) |
| 0x70 | 4 | Folders Table unknown |
| 0x74 | 4 | Unknown, Folders Table size-related |
| 0x78 | 4/8 | Files Table offset (8 bytes in DATA) |
| 0x7C | 4 | Files Table Length (medias) (Only in no DATA) |
| 0x80 | 4 | Files Table unknown |
| 0x84 | 4 | Unknown, Files Table size-related |
- The FolderMap and FileMap still unknown. They are tables of uint32.
- The BlockMap is a map of the blocks in the filestore. An entry in the BlockMap is 2 uint32: {uint32 start_block; uint32 end_block; }. This is still being researched. (You can use 3DSExplorer to see those maps.
Summary Drawing
初始化
当一个存储FLASH包含所有xFFFF块,它假定由游戏墨盒未初始化,初始化默认数据的地方,不提示用户的情况下。0xFFFFFFFF的块未初始化的数据。当创建一个非游戏卡的秘技和其他图像/文件,它的最初所有0xFFFFFFFF的,直到它的一些块格式化,加密数据覆盖。 When a save FLASH contains all xFFFF blocks it's assumed uninitialized by the game cartridges and it initializes default data in place, without prompting the user. The 0xFFFFFFFF blocks are uninitialized data. When creating a non-gamecard savegame and other images/files, it's initially all 0xFFFFFFFF until it's formatted where some of the blocks are overwritten with encrypted data.
我得到了一个新的游戏 SplinterCell3D-Pal ,它的128KB存档除去开头的0x10 byte是‘Z’(大写),其余都为0xFF --Elisherer 22:41 2011年10月15日(CEST)
事实
如果你发现二进制文件的一些事实把它们分享到这里:
- 从一个存档到这个游戏在这个分区的另一个游戏备份,后者全部image的头部变为随机位置.. --Elisherer 22:41 2011年10月15日(CEST)
从一个“随机”位置在分区和整个图像头的最后一个文件,保存到另一个游戏备份..
工具
- 3dsfuse 支持读写游戏存档。在mount的FUSE文件系统中,/output.sav是raw FLASH save-image。When the save was modified, a separate tool to update the MAC must be used with /clean.sav, prior to writing output.sav to a gamecard.
- 3DSExplorer supports reading of savegames, it doesn't support reading the new encrypted savegames and maybe in the future it will support modifying (some of the modyfing code is already implemented).